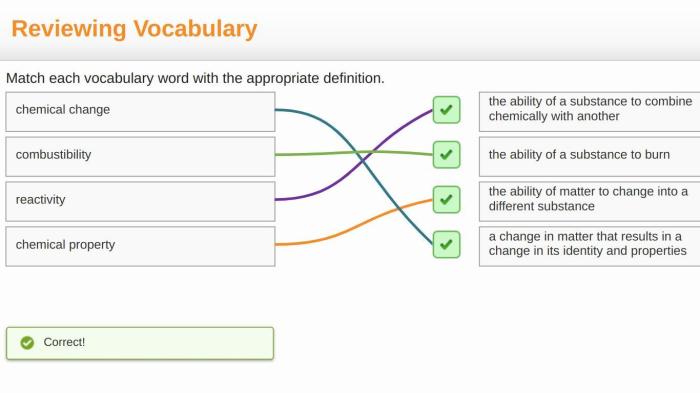
Match each network sniffing method with the correct definition. – Network sniffing is a powerful technique used to capture and analyze network traffic. It involves monitoring data packets as they traverse a network, providing valuable insights into network activity. This comprehensive guide explores various network sniffing methods, empowering you with the knowledge to effectively monitor and secure your networks.
From passive sniffing to active sniffing, promiscuous mode to port mirroring, we delve into the intricacies of each technique, discussing their advantages and disadvantages. Additionally, we provide real-world examples and address common FAQs to ensure a thorough understanding of network sniffing.
Network Sniffing Methods
Network sniffing is the process of intercepting and analyzing network traffic. It can be used for a variety of purposes, including troubleshooting network problems, detecting security breaches, and monitoring network activity.
There are two main types of network sniffing: passive sniffing and active sniffing.
Passive Sniffing, Match each network sniffing method with the correct definition.
Passive sniffing involves listening to network traffic without sending any packets of its own. This type of sniffing is typically used for troubleshooting network problems and detecting security breaches.
- Example passive sniffing techniques include using the tcpdump and Wireshark tools.
Active Sniffing
Active sniffing involves sending packets of its own in order to elicit responses from other devices on the network. This type of sniffing is typically used for network discovery and mapping.
- Example active sniffing techniques include using the nmap and arp-scan tools.
Promiscuous Mode
Promiscuous mode is a network interface setting that allows a network interface card (NIC) to receive all traffic on a network, regardless of its destination.
- Promiscuous mode is typically used for network sniffing.
- The main advantage of using promiscuous mode is that it allows a network sniffer to see all traffic on a network.
- The main disadvantage of using promiscuous mode is that it can increase the amount of traffic that a network sniffer receives, which can slow down the network.
Port Mirroring
Port mirroring is a technique that allows a network administrator to copy traffic from one port on a switch to another port.
- Port mirroring is typically used for network troubleshooting and monitoring.
- The main advantage of using port mirroring is that it allows a network administrator to monitor traffic on a network without having to connect to the network directly.
- The main disadvantage of using port mirroring is that it can increase the amount of traffic that a network sniffer receives, which can slow down the network.
Network Taps
Network taps are devices that allow a network administrator to monitor traffic on a network without having to connect to the network directly.
- Network taps are typically used for network troubleshooting and monitoring.
- The main advantage of using network taps is that they do not increase the amount of traffic that a network sniffer receives, which can help to improve network performance.
- The main disadvantage of using network taps is that they can be more expensive than other network sniffing methods.
Question Bank: Match Each Network Sniffing Method With The Correct Definition.
What are the ethical considerations of network sniffing?
Network sniffing can raise ethical concerns, as it involves capturing and analyzing network traffic that may contain sensitive data. It is essential to obtain proper authorization and adhere to ethical guidelines to avoid privacy violations.
What are some examples of network sniffing tools?
Popular network sniffing tools include Wireshark, tcpdump, and Snort. These tools provide advanced capabilities for capturing, analyzing, and filtering network traffic.
What are the advantages of using promiscuous mode?
Promiscuous mode allows a network interface to receive all traffic on a network segment, regardless of the destination address. This provides a comprehensive view of network activity, but it can also increase the volume of data to be processed.